⏱ 5 min
In our digital age, cyber risks are becoming increasingly relevant for companies. While the focus was only on certain industries in the past, every company is potentially at risk today.
Cyber risks in Switzerland
It’s rare that a couple of weeks pass by without reports of a new cyber attack. In Switzerland, too, it is by no means just larger companies – as we’ve seen recently with RUAG1, Comparis2 and Media Markt3 that are affected.
SMEs can also fall victim to such incidents as the example of a Thurgau window manufacturer shows: Following a cyber attack in 2019, the computer-controlled machinery no longer worked. Malware was slipped into the company in the attachment of an inconspicuous email, production ground to a halt and the company ultimately even went bankrupt.4
This example is not an isolated case. The British market research company comparitech estimated that Switzerland lost USD 728 million to cyber attacks in 20205. In addition, the number of incidents in 2021 doubled compared to the previous year.6 What’s more, many companies simply go ahead and pay the demands of ransomware or other attacks, so it can be assumed that the number of unreported cases is high. Some companies do so in order to protect their reputation; others feel they have no other choice if they want to restart operations since all their business-relevant data and back-ups have been encrypted in the attack. However, incidents often still become public knowledge at some point as a recent case in a municipality in western Switzerland shows.7
Urgent need for action at many companies
At the same time, Florian Schütz, the federal Cyber Security Delegate, states in an interview with Swiss newspaper NZZ: “Many companies I talk to have no idea how well they are protected against cyber attacks by their provider. Does the provider automatically fend off attacks from known attackers?”8. In order to mitigate this problem and make it easier for companies to find a provider, the Swiss digital security organisation “Allianz Digitale Sicherheit Schweiz” has launched its CyberSeal certificate9. The certificate is awarded to providers who meet the required cyber security measures.
The fact that organisations are often inadequately equipped to deal with cyber risks is also illustrated in another case: A security vulnerability in Microsoft Exchange servers, which are in widespread use, has been known for over a year and is actively abused by cyber criminals. Still, the National Cyber Security Centre (NCSC) recently had to once again inform over 200 companies and individual municipalities about the urgently needed security update.10
The lack of cyber risk assessment takes many companies into unchartered territory. The impact due to operational risks (business disruption and downtime, ransom payments or reputational damage), but also regulatory risks (e.g. penalties for insufficient data protection) can be far-reaching. And the trend is set to gather pace amid increasing digitalisation, use of data and changing business models.11
Structured measures are needed
To minimise risks, companies should adopt a structured, risk-based approach as the basis for targeted measures. The NCSC distinguishes between technical and organisational measures12. Technical measures include, for example, regular back-ups and security updates, effective virus protection and firewalls. Another technical measure – and one that’s often forgotten – is the ongoing and active administration of user authorisation. Organisational measures, on the other hand, include topics such as regular assessments of cyber risks, clear division of responsibilities (including between the company and the external IT service provider) and employee awareness (e.g. anti-phishing training). Many Swiss companies do not yet have predefined emergency plans setting out the procedures and responsibilities in the event of an incident. Ultimately, however, all measures must be carefully weighed against the associated risks and costs.
Role of internal audit
Developing balanced measures to mitigate risks is a core competence of internal audit. To minimise cyber risks and strengthen resilience against cyber attacks it makes absolute sense to combine the capabilities of internal audit with the technical expertise of cyber security experts.
Close cooperation between internal audit and cyber security experts has extensive advantages for companies. For example, improvement measures and suggestions for cyber security can be integrated with little additional effort into existing processes as part of the internal audit. Furthermore, companies can save themselves the high costs associated with establishing their own dedicated cyber security department – an advantage for SMEs in particular.
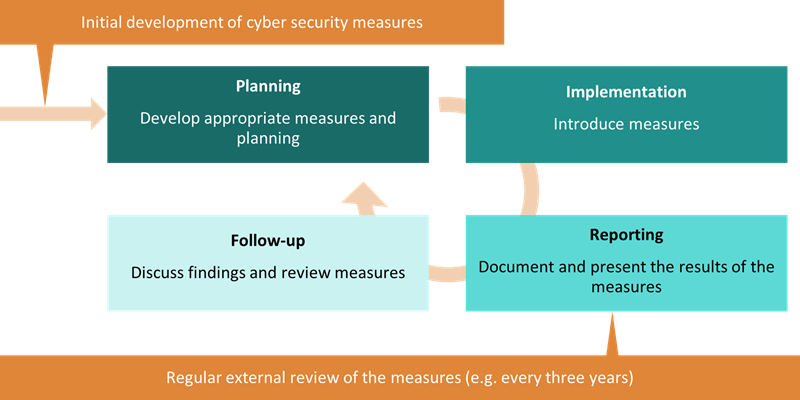
The following process illustrates how measures to increase cyber security can be integrated into internal audit:
- Planning
CyberCheck for SMEs. It is recommended to involve cyber security experts for a more comprehensive analysis and initial development of security measures.
- Implementation
Together with your internal audit department, cyber security experts carry out a security assessment. This is a technical examination of the company’s existing measures and protective mechanisms. This systematic evaluation looks at your current posture.
- Reporting
Existing security gaps and risks are highlighted and presented to your management and other relevant stakeholders. This could, for example, be directly linked to reporting of other areas covered by your internal audit.
- Follow-up
Together, the findings are used to identify improvement measures, define responsibilities and take next steps. Regular reviews and further development are the responsibility of the internal audit department, which integrates these activities into its existing processes.
It is also advisable to conduct regular IT audits in order to get a professional third-party opinion on the measures taken and the security concept as well as to anticipate current developments. This is because, in contrast to the security assessments carried out annually as part of the internal audit, an IT audit does not focus on the technical aspects but on the organisational and conceptual aspects of risk mitigation. The findings of the IT audit can then also flow into the regular security assessments.
Conclusion
Integrating the review of cyber risks into the internal audit is an elegant solution to minimise such risks in a structured approach. It means existing knowledge and established processes can be leveraged, making an important contribution to a company’s security and business success.